Oct 9, 2023
The theme of the CTF is 'Generative AI: Transforming cyber defenders of tomorrow.' Indeed many challenges seem readily solvable with ChatGPT and a little understanding.
So we can easily open this with Wireshark and observe that it has a list of 10-byte HID data:
ChatGPT is actually very good at observing it:
Examining the data, the following pattern seems evident:
- Byte 1: It's consistently
0x02across all packets. This could be indicative of the state of a button (possibly the right button, as previously mentioned).- Byte 2: Always
0x00. This is likely a static or reserved byte.- Bytes 3 and 4: These bytes change frequently and are possibly related to movement. They likely represent a signed 16-bit value for the X-direction movement, given the variability. In USB HID mouse reports, it's common for these bytes to represent mouse movement as 2's complement signed integers.
- Bytes 5 and 6: Like Bytes 3 and 4, these bytes show frequent changes. They likely represent movement in the Y-direction, also as 2's complement signed integers.
- Bytes 7-10: These bytes are consistently
0x00, indicating they might be reserved or not used for this particular device or mode of operation.Given the pattern, this data very likely originates from a USB HID mouse:
- The
0x02indicates the state of the right button (or possibly another button or feature).- Bytes 3-4 and 5-6 suggest movements in the X and Y directions, respectively.
- The variability in the movement bytes aligns with typical mouse behavior – small changes in values corresponding to minute mouse movements.
This interpretation is further bolstered by the signed 16-bit values. When viewed in a signed context, some values represent slight movements to the left or up (negative values) while others indicate movements to the right or down (positive values).
It is also possible to ask ChatGPT to plot it. After a bit tweaking we get something like this:
We get something like this:
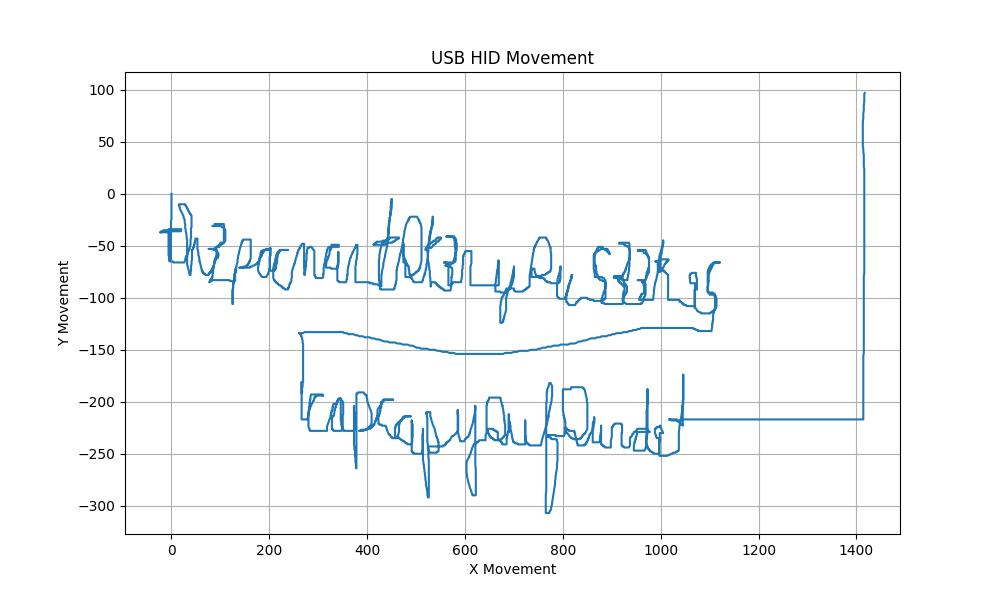
It is actually a bit hard to read, but after trial and error we get th3 pacman t0ken you s33k is capcapyouf0undit.
Very classical book cipher:
Bascially we have to find the entry point http://example.com/Cyb3rg0vAdmin/Login.aspx. The Cyb3rg0vAdmin part is really hard to find without a hint from the organizer…
I feel their announcement can really be improved by ChatGPT :)
Welcome to 2023 Raymond James CTF. Here are the rules of engagement for this year's CTF.
- Players must be onsite and on the game floor to participate in the Raymond James CTF. Under no circumstances will anyone be allowed to participate remotely. Any team found making use of remote participants will be disqualified and asked to leave the game floor.
- We are not providing or guaranteeing Internet access. Do not expect to have Internet access via the CTF network.
- Your team is not authorized to plug any equipment into the CTF network with the exception of one laptop computer per onsite team player. If your team is noted as having any additional equipment plugged into the CTF network your team will be disqualified and asked to leave the game floor. There is no flexibility on this rule, no second chances…consider this as the only warning.
- Teams are expected to provide their own laptop computer systems to plug in to the CTF network. Do not try to read between the lines on this…it's pretty straightforward, 1 laptop computer plugged into the CTF network per onsite team player…no exceptions. If your team brings additional laptop computers, they are not authorized to be plugged into the CTF network. A tower system may be used as a substitute for a laptop. If you have any questions on the type of system you are allowed to use, check with the Support Team prior to the event.
- Stay in your lane. Your team is not authorized to attack, scan or otherwise interfere with any assets that are not provided directly as a target address (Web or IP) assigned to your team. There are no exceptions to this rule. If your team is identified as violating this rule your team will be disqualified and asked to leave the game floor. This includes but is not limited to the use of additional wireless equipment that has not been pre-approved, setting up your own access point, jamming, interfering, collecting traffic or overpowering the Raymond James access points etc, etc.
- Your team is not authorized to bridge anything to the CTF network. This includes but is not limited to wireless Internet, 3G/4G mobile connections, etc, etc. There are no exceptions to this rule. If your team is identified as violating this rule your team will be disqualified and asked to leave the game floor.
- If your team is tasked with a physical security challenge, we will provide you with the minimal necessary tools to complete the task. Your team is not expected to or authorized to bring additional equipment. Any physical security challenges received must remain in a provable working condition upon completion of the task.
- Do NOT blindly scan for targets, it's a waste of time and bandwidth. When your team receives a target, if you feel it necessary to scan that target you are authorized to do so. In most cases, you will be provided an address (Web or IP) and port number. Teams are not authorized to attack each other. If you find yourself in question as to the target you are proceeding after, get clarification. Violations of this rule will get your team disqualified and asked to leave the game floor.
- Expect to retrieve t0k3ns, plant t0k3ns and solve a variety of challenges. Once you have a t0k3n, unless otherwise directed, move on to the next challenge.
- The laptops your team brings should have a virtual machine software installed such as VMware, or VirtualBox. At least one team laptop should have wireless capability. All laptops should have the capability to connect to an Ethernet network.
- Most important…if you have questions before the competition contact the Support Team at [email protected]. Once teams are onsite ask the Command Center Staff for any clarifications.
Interacting with Gam3z Inc Support/RJ Staff:
- We've spent many hours putting this event together. Trust me…when something isn't working right, we're more stressed out than you!
- Have patience, if you have a question, issue or problem we will address it as quickly as possible.
- We understand you're under a time limit … so are we. If a problem arises that negatively impacts the game, we'll be actively working through it.
- Don't consider this as "Us vs Them"…if you have questions please ask.
- We've provided email support and ask that you be respectful in your communications with our team.
ChatGPT version:
Welcome to the exhilarating 2023 Raymond James Capture The Flag (CTF) challenge! As we gear up for a riveting competition, here's a rundown of the game rules to ensure a smooth and enjoyable experience for all participants:
- Players, your presence on the game floor is essential for partaking in the Raymond James CTF adventure. Unfortunately, remote participation isn't an option this year. If a team is discovered utilizing remote players, a gentle exit from the game floor will be required following disqualification.
- While we strive for a seamless experience, we're unable to promise internet connectivity. The CTF network might not provide internet access, hence come prepared.
- Your team is permitted to connect one laptop per onsite player to the CTF network. Any deviation noted, such as additional equipment, will regrettably lead to disqualification and a request to vacate the game floor. This rule is steadfast with no room for negotiation, so consider this a friendly heads-up.
- It's expected that each team comes with their own laptop for plugging into the CTF network - a simple one laptop per onsite player rule. In case of additional laptops, they're to remain disconnected from the CTF network. However, a tower system can replace a laptop if preferred. Any queries regarding permissible system types? Feel free to reach out to the Support Team before the event.
- Maintaining your focus is key! Your team should only interact with designated target addresses (Web or IP). Any unapproved interactions, including, but not limited to, the usage of unauthorized wireless equipment or setting up personal access points, will unfortunately result in disqualification and a polite request to leave the game floor.
- Bridging external networks to the CTF network is not allowed, this includes wireless or mobile connections. Adhering to this rule is crucial to continue enjoying the game.
- For physical security challenges, we'll equip you with essential tools. Your team isn't required to bring extra equipment. It's important to ensure the challenges remain in a demonstrable working condition post-completion.
- Scanning indiscriminately for targets isn't advisable as it's both time and bandwidth consuming. Upon receiving a target, feel free to scan if deemed necessary. Missteps in this rule may lead to disqualification, so when in doubt, seek clarification.
- Engage in a quest for tokens, plant them and unravel a myriad of challenges. Once a token is secured, gear up for the next thrilling challenge!
- Your team's laptops should be outfitted with virtual machine software like VMware or VirtualBox. Ensuring at least one laptop has wireless capability and all can connect to an Ethernet network will set you up for success.
- Queries are welcome! Prior to the competition, direct your questions to the Support Team at [email protected]. Onsite, the Command Center Staff is at your disposal for any clarifications.
Interactions with Gam3z Inc Support/RJ Staff:
- The diligent preparation for this event is a testament to our commitment. Should any hiccup occur, rest assured, we're on it even before the stress kicks in!
- Patience is a virtue. We're here to address your queries, issues or concerns promptly.
- We share the thrill and the time crunch. Any game-affecting issues will receive immediate attention.
- This is a collaborative endeavor, not a "Us vs Them" scenario. Your questions help us all, so feel free to ask.
- Our email support is at your service, and respectful communication is much appreciated.
We're thrilled to have you at the 2023 Raymond James CTF and wish you an exciting and intellectually stimulating competition ahead!
I will have you decide which version is better :)